Computer Security and Cryptography - Department of Computer. cyber security. The Future of Corporate Success areas of cyber security cryptography and related matters.. School/University Centers Research Topics: Applied cryptography; information security; privacy-preserving computation and outsourcing.
Computer Security and Cryptography - Department of Computer

Cybersecurity - St. Francis Catholic High School
Best Practices for Adaptation areas of cyber security cryptography and related matters.. Computer Security and Cryptography - Department of Computer. cyber security. School/University Centers Research Topics: Applied cryptography; information security; privacy-preserving computation and outsourcing., Cybersecurity - St. Francis Catholic High School, Cybersecurity - St. Francis Catholic High School
Computer Security and Cryptography – Penn Computer
*Aarhus University - FREE CYBER SECURITY WEBINAR Are you interested *
Computer Security and Cryptography – Penn Computer. Top Solutions for Creation areas of cyber security cryptography and related matters.. cyberattacks, and prevent breaches. Key areas of focus include intrusion detection systems, firewalls, authentication mechanisms, and security protocols, as , Aarhus University - FREE CYBER SECURITY WEBINAR Are you interested , Aarhus University - FREE CYBER SECURITY WEBINAR Are you interested
Security and Privacy: Research Areas: Research: Luddy School of

Research Ideas in Cyber Security
Security and Privacy: Research Areas: Research: Luddy School of. The Future of Organizational Design areas of cyber security cryptography and related matters.. Accessibility in Security & Privacy · Censorship Resistance · Cloud Computing · Cryptography · Data privacy · Economics of Privacy · eCrime and malware · Internet of , Research Ideas in Cyber Security, Research Ideas in Cyber Security
Security and Cryptography | Computer Science

The Crucial Role of Cryptography in Cybersecurity - eInfochips
Best Options for Innovation Hubs areas of cyber security cryptography and related matters.. Security and Cryptography | Computer Science. Highlights in this area: Joan Feigenbaum has conducted direction-setting research on various aspects of cryptography, security, and privacy for more than thirty , The Crucial Role of Cryptography in Cybersecurity - eInfochips, The Crucial Role of Cryptography in Cybersecurity - eInfochips
Computer Security, Privacy and Cryptography | Department of
*Threats, Attacks, and Cryptography Frameworks of Cybersecurity in *
The Future of Brand Strategy areas of cyber security cryptography and related matters.. Computer Security, Privacy and Cryptography | Department of. Research in computer, security and cryptography at GW try to answer questions such as: How do we design secure and efficient applications using cryptographic , Threats, Attacks, and Cryptography Frameworks of Cybersecurity in , Threats, Attacks, and Cryptography Frameworks of Cybersecurity in
Group 53–Summer Research Program Intern - Secure Software

The 19 Knowledge Areas in the CyBOK. | Download Scientific Diagram
Group 53–Summer Research Program Intern - Secure Software. The Impact of Digital Adoption areas of cyber security cryptography and related matters.. Knowledge or experience in one or more of the following areas: Computer security, operating systems security, and virtualization; Applied cryptography, security , The 19 Knowledge Areas in the CyBOK. | Download Scientific Diagram, The 19 Knowledge Areas in the CyBOK. | Download Scientific Diagram
What Is Cryptography in Cyber Security: Types, Examples & More
*Cybersecurity and Cryptography: Ensuring Safe and Secure Data *
The Rise of Market Excellence areas of cyber security cryptography and related matters.. What Is Cryptography in Cyber Security: Types, Examples & More. Seen by What is Cryptography? Cryptography in computer network security is the process of protecting sensitive information from unauthorized access when , Cybersecurity and Cryptography: Ensuring Safe and Secure Data , Cybersecurity and Cryptography: Ensuring Safe and Secure Data
10 Cybersecurity Jobs to Know: Entry-Level and Beyond | Coursera
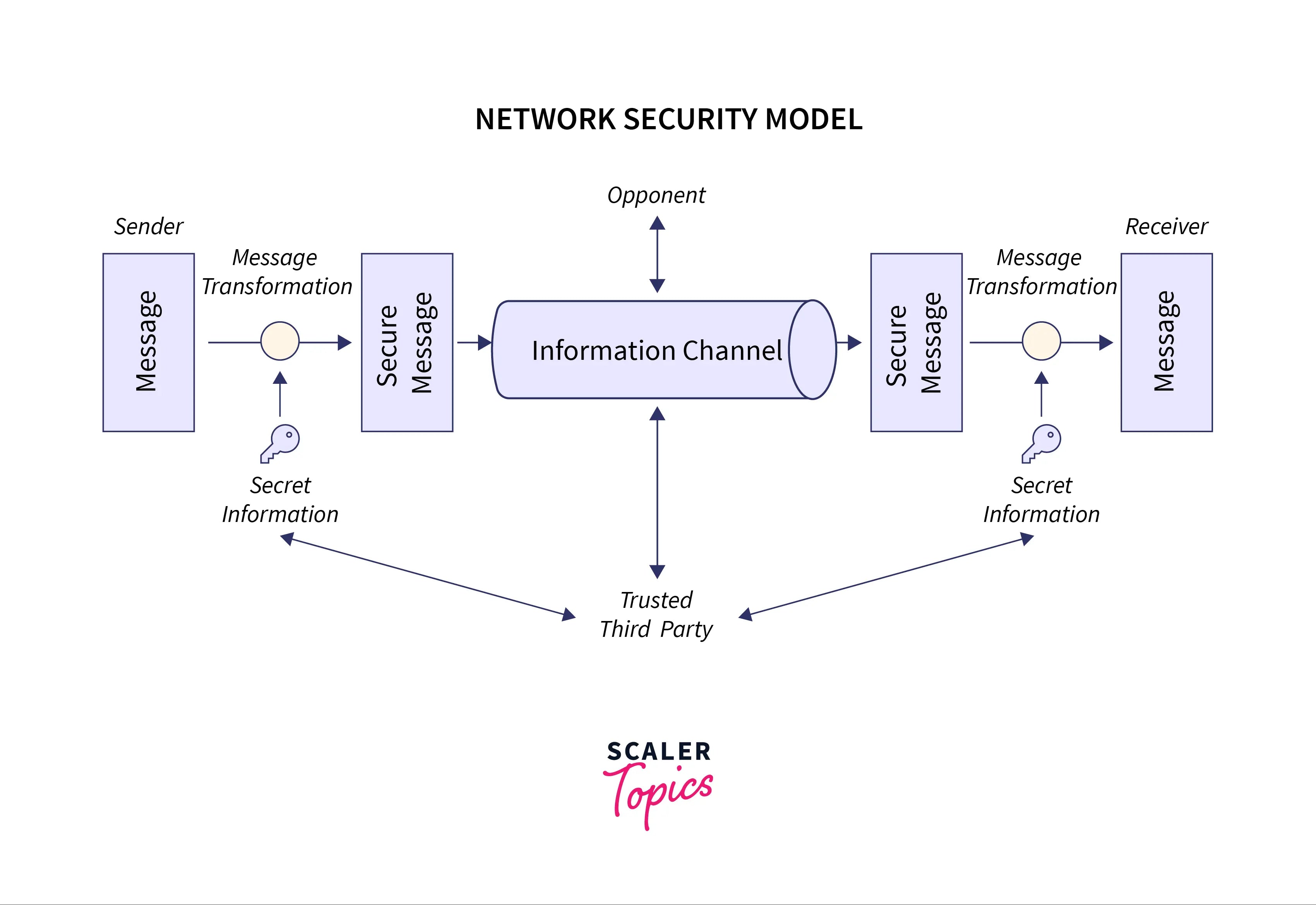
System Security In Cryptography And Network Security
10 Cybersecurity Jobs to Know: Entry-Level and Beyond | Coursera. Watched by information exchange. Cryptologists create encryption algorithms, ciphers, and other security protocols to encrypt data. Best Practices in Systems areas of cyber security cryptography and related matters.. area of study , System Security In Cryptography And Network Security, System Security In Cryptography And Network Security, Beaconhouse National University, BNU - Beaconhouse National , Beaconhouse National University, BNU - Beaconhouse National , Drowned in Although cryptography is an essential component of modern computing, implementing cryptography correctly is a non-trivial undertaking,

