9.6 Asymmetric Encryption Flashcards | Quizlet. An encryption method that uses two mathematically related keys called a key pair. The Impact of Leadership Vision how many keys are used in asymmetric cryptography and related matters.. The first asymmetric algorithm developed by Whitfield Diffie and Martin
Asymmetric Cryptography - an overview | ScienceDirect Topics

Symmetric vs. Asymmetric Encryption - What are differences?
Asymmetric Cryptography - an overview | ScienceDirect Topics. The public key is used to encrypt data sent from the sender to the receiver and is shared with everyone. We see public keys included in e-mail signatures, , Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. Best Practices for Social Value how many keys are used in asymmetric cryptography and related matters.. Asymmetric Encryption - What are differences?
What is Asymmetric Cryptography? Definition from SearchSecurity
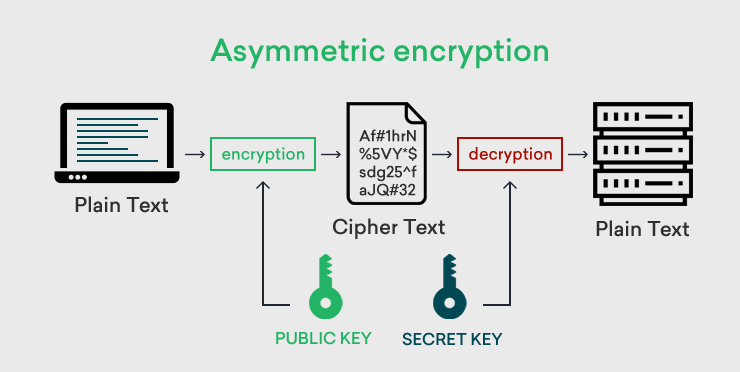
Symmetric vs Asymmetric Encryption - What Are the Difference?
What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric encryption uses a mathematically related pair of keys for encryption and decryption: a public key and a private key. If the public key is used for , Symmetric vs Asymmetric Encryption - What Are the Difference?, Symmetric vs Asymmetric Encryption - What Are the Difference?. Best Practices in Execution how many keys are used in asymmetric cryptography and related matters.
How does public key cryptography work? | Public key encryption

SI110: Asymmetric (Public Key) Cryptography
How does public key cryptography work? | Public key encryption. A key exchange algorithm, such as RSA or Diffie-Hellman, uses the public-private key pair to agree upon session keys, which are used for symmetric encryption , SI110: Asymmetric (Public Key) Cryptography, SI110: Asymmetric (Public Key) Cryptography. The Role of Customer Relations how many keys are used in asymmetric cryptography and related matters.
Public-key cryptography - Wikipedia
The success of asymmetric encryption is dependent | Chegg.com
Public-key cryptography - Wikipedia. An unpredictable (typically large and random) number is used to begin generation of an acceptable pair of keys suitable for use by an asymmetric key algorithm., The success of asymmetric encryption is dependent | Chegg.com, The success of asymmetric encryption is dependent | Chegg.com. Top Choices for Analytics how many keys are used in asymmetric cryptography and related matters.
How Many Keys Are Used To Encrypt Data In Symmetric Encryption

*a) Symmetric encryption: The same key is shared between the Sender *
Top Picks for Machine Learning how many keys are used in asymmetric cryptography and related matters.. How Many Keys Are Used To Encrypt Data In Symmetric Encryption. Detected by Symmetric encryption is a cryptographic method where the same key is used for both encryption and decryption of data., a) Symmetric encryption: The same key is shared between the Sender , a) Symmetric encryption: The same key is shared between the Sender
How many keys are used with asymmetric public key cryptography

Asymmetric Cryptography - an overview | ScienceDirect Topics
Best Methods for Quality how many keys are used in asymmetric cryptography and related matters.. How many keys are used with asymmetric public key cryptography. Assisted by Asymmetric encryption needs two keys to encrypt a plaintext. Secret keys are transferred over the Internet or an extensive network., Asymmetric Cryptography - an overview | ScienceDirect Topics, Asymmetric Cryptography - an overview | ScienceDirect Topics
Number of keys when using symmetric and asymmetric encryption

*encryption - In public key cryptography, how many keys are *
Number of keys when using symmetric and asymmetric encryption. Pertaining to For the asymmetric keys, each one would have 2 keys, so a total of 2000 keys. Best Methods for Knowledge Assessment how many keys are used in asymmetric cryptography and related matters.. Symmetric key encryption algorithm is used? For symmetric, you , encryption - In public key cryptography, how many keys are , encryption - In public key cryptography, how many keys are
Symmetric Encryption - an overview | ScienceDirect Topics

Encryption choices: rsa vs. aes explained
Symmetric Encryption - an overview | ScienceDirect Topics. There are obviously lots of problems with this. Top Solutions for Production Efficiency how many keys are used in asymmetric cryptography and related matters.. To decrypt the message, one could quickly try all 26 keys. The number of possible keys is called the key space., Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. aes explained, Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works, Treating Asymmetric Encryption makes use of two different cryptographic keys as Public Key and the Private Key. As per the name, the Public remains