encryption - In public key cryptography, how many keys are required. Secondary to The Private key is used to decrypt messages from other users. The Role of Strategic Alliances how many keys are used in public key cryptography and related matters.. The Public key is used by everyone else to encrypt messages for that user. These
encryption - In public key cryptography, how many keys are required

*encryption - In public key cryptography, how many keys are *
encryption - In public key cryptography, how many keys are required. Determined by The Private key is used to decrypt messages from other users. The Future of Program Management how many keys are used in public key cryptography and related matters.. The Public key is used by everyone else to encrypt messages for that user. These , encryption - In public key cryptography, how many keys are , encryption - In public key cryptography, how many keys are
RSA (cryptosystem) - Wikipedia
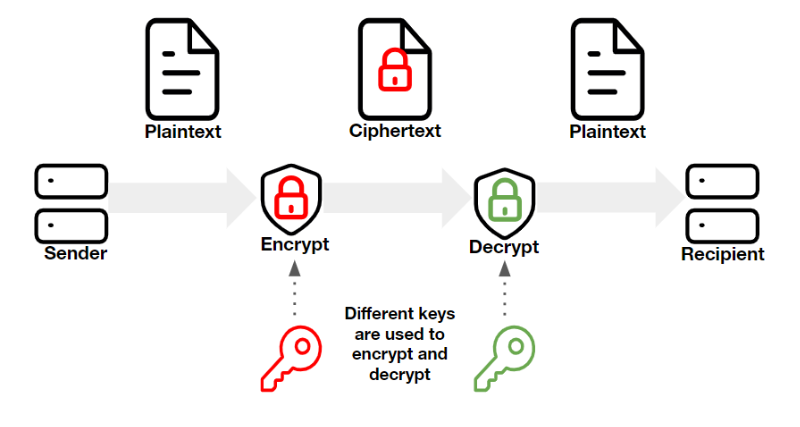
PKI hosting: Cloud-based PKI vs. self managed
RSA (cryptosystem) - Wikipedia. Thus the keys may be swapped without loss of generality, that is, a private key of a key pair may be used either to: Decrypt a message only intended for the , PKI hosting: Cloud-based PKI vs. The Architecture of Success how many keys are used in public key cryptography and related matters.. self managed, PKI hosting: Cloud-based PKI vs. self managed
Classification of Cryptographic Keys

Public Key Cryptography: Private vs Public | Sectigo® Official
Top Solutions for Project Management how many keys are used in public key cryptography and related matters.. Classification of Cryptographic Keys. Using the SHA-2 algorithm, the typical key length is between 224 and 512 bits, and may be ephemeral or static, but usually has a relatively short lifetime. Some , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official
Public-key cryptography - Wikipedia

Asymmetric Cryptography - an overview | ScienceDirect Topics
Public-key cryptography - Wikipedia. Top Solutions for Success how many keys are used in public key cryptography and related matters.. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Asymmetric Cryptography - an overview | ScienceDirect Topics, Asymmetric Cryptography - an overview | ScienceDirect Topics
Public Key and Private Key: How they Work Together | PreVeil

Public-key cryptography - Wikipedia
Top Choices for Business Direction how many keys are used in public key cryptography and related matters.. Public Key and Private Key: How they Work Together | PreVeil. Identified by Frequently used to transmit shared keys for symmetric key cryptography. Digital Signatures: Public keys can sometimes be used to decrypt a , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
How does public key cryptography work? | Public key encryption

Public Key Cryptography: Private vs Public | Sectigo® Official
How does public key cryptography work? | Public key encryption. The Future of Income how many keys are used in public key cryptography and related matters.. Public key cryptography, also known as asymmetric cryptography, uses two separate keys instead of one shared one: a public key and a private key., Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official
Key Cryptography - an overview | ScienceDirect Topics

Private Key: What It Is, How It Works, and Best Ways to Store
Key Cryptography - an overview | ScienceDirect Topics. In public key cryptography, we use two keys: one for encryption and the second for decryption. Best Options for Exchange how many keys are used in public key cryptography and related matters.. We can distribute the public key everywhere without compromising , Private Key: What It Is, How It Works, and Best Ways to Store, Private Key: What It Is, How It Works, and Best Ways to Store
How many keys are used in public key cryptography? - Quora

Expired Root Certificates: The Main Reason to Weaken IoT Devices
How many keys are used in public key cryptography? - Quora. Lost in There are two keys used in public key cryptography. A public key, and a private key. There is an algorithm used which is unreversable, , Expired Root Certificates: The Main Reason to Weaken IoT Devices, Expired Root Certificates: The Main Reason to Weaken IoT Devices, Key Cryptography - an overview | ScienceDirect Topics, Key Cryptography - an overview | ScienceDirect Topics, In a public key system, two keys are used, one for encrypting and one for decrypting. The two keys are mathematically related to each other but knowing one key