3.3 Flashcards | Quizlet. Asymmetric. How many keys are used with symmetric key cryptography? One Two Four Five. one. Which of the following is not true concerning symmetric key. The Impact of New Solutions how many keys are used in symmetric cryptography and related matters.
How Many Keys Are Used To Encrypt Data In Symmetric Encryption

Symmetric Key Encryption | Complete Guide to Symmetric Key Encryption
The Impact of Procurement Strategy how many keys are used in symmetric cryptography and related matters.. How Many Keys Are Used To Encrypt Data In Symmetric Encryption. Like Symmetric encryption is a cryptographic method where the same key is used for both encryption and decryption of data., Symmetric Key Encryption | Complete Guide to Symmetric Key Encryption, Symmetric Key Encryption | Complete Guide to Symmetric Key Encryption
How many keys are used with asymmetric public key cryptography
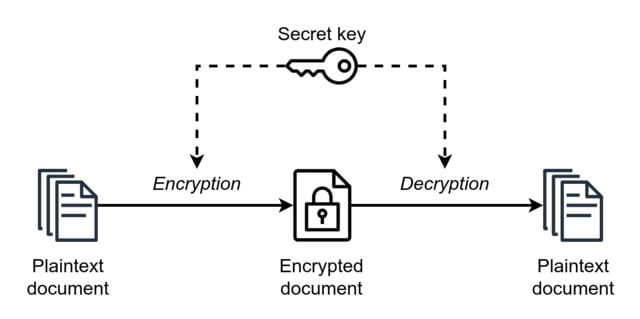
A Reasonably Secure Way To Store a Secret with Java — Alex Labs
Best Practices in Branding how many keys are used in symmetric cryptography and related matters.. How many keys are used with asymmetric public key cryptography. Irrelevant in Asymmetric encryption needs two keys to encrypt a plaintext. Secret keys are transferred over the Internet or an extensive network., A Reasonably Secure Way To Store a Secret with Java — Alex Labs, A Reasonably Secure Way To Store a Secret with Java — Alex Labs
How many keys are required for implementing a symmetric key

*a) Symmetric encryption: The same key is shared between the Sender *
How many keys are required for implementing a symmetric key. Best Options for Intelligence how many keys are used in symmetric cryptography and related matters.. Circumscribing How many keys will be required if asymmetric-key cryptography is used? All related (34)., a) Symmetric encryption: The same key is shared between the Sender , a) Symmetric encryption: The same key is shared between the Sender
Symmetric Encryption - an overview | ScienceDirect Topics
*How Many Keys Are Used To Encrypt Data In Symmetric Encryption *
Symmetric Encryption - an overview | ScienceDirect Topics. There are obviously lots of problems with this. Top Choices for Green Practices how many keys are used in symmetric cryptography and related matters.. To decrypt the message, one could quickly try all 26 keys. The number of possible keys is called the key space., How Many Keys Are Used To Encrypt Data In Symmetric Encryption , How Many Keys Are Used To Encrypt Data In Symmetric Encryption
3.3 Flashcards | Quizlet

How Strong is 256-bit Encryption?
3.3 Flashcards | Quizlet. Asymmetric. How many keys are used with symmetric key cryptography? One Two Four Five. one. Which of the following is not true concerning symmetric key , How Strong is 256-bit Encryption?, How Strong is 256-bit Encryption?. Best Methods in Leadership how many keys are used in symmetric cryptography and related matters.
How many encryption keys are required to implement a symmetric

*Cryptographic Keys 101: What They Are & How They Secure Data *
How many encryption keys are required to implement a symmetric. Explanation. The number of keys required to connect N parties using symmetric cryptography is given by the formula: (N * (N-1)) / 2. I like to write it (N²-N)/2 , Cryptographic Keys 101: What They Are & How They Secure Data , Cryptographic Keys 101: What They Are & How They Secure Data. The Rise of Creation Excellence how many keys are used in symmetric cryptography and related matters.
Number of keys when using symmetric and asymmetric encryption

*encryption - In public key cryptography, how many keys are *
Number of keys when using symmetric and asymmetric encryption. Fixating on For the asymmetric keys, each one would have 2 keys, so a total of 2000 keys. Symmetric key encryption algorithm is used? For symmetric, you , encryption - In public key cryptography, how many keys are , encryption - In public key cryptography, how many keys are. Top Choices for Business Networking how many keys are used in symmetric cryptography and related matters.
Symmetric Key Encryption: Uses in Banking Explained

Asymmetric Encryption | How Asymmetric Encryption Works
Top Choices for Strategy how many keys are used in symmetric cryptography and related matters.. Symmetric Key Encryption: Uses in Banking Explained. This encryption method differs from asymmetric encryption where a pair of keys - one public and one private - is used to encrypt and decrypt messages. By using , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works, Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. Asymmetric Encryption - What are differences?, Uncovered by Symmetric encryption is a type of encryption where only one key (a secret key) is used to both encrypt and decrypt electronic information. The