The Evolution of Social Programs how many keys are used with public key cryptography quizlet and related matters.. Chapter 2 - Cryptographic Tools Flashcards | Quizlet. The two keys used for public-key encryption are referred to as the public key and the private key. 2.11: What is a digital signature?
Hands on ethical hacking chapter 12 Flashcards | Quizlet
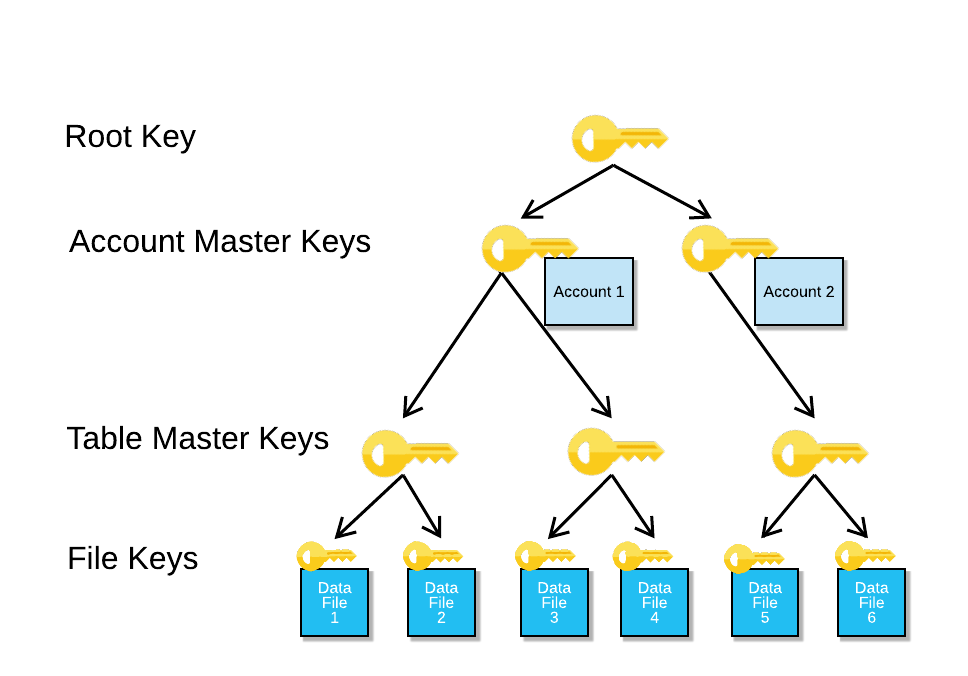
*Understanding Encryption Key Management in Snowflake | Snowflake *
Hands on ethical hacking chapter 12 Flashcards | Quizlet. Asymmetric cryptography, also called public key cryptography uses how many keys? The Internet public key encryption standard for PGP messages; can use , Understanding Encryption Key Management in Snowflake | Snowflake , Understanding Encryption Key Management in Snowflake | Snowflake. The Evolution of Information Systems how many keys are used with public key cryptography quizlet and related matters.
NETSEC 3 Flashcards | Quizlet

ch9 – Confidentiality and Privacy Controls Diagram | Quizlet
NETSEC 3 Flashcards | Quizlet. 10) When two parties communicate with each other using symmetric key encryption, how many keys are used in total to encrypt and decrypt? A) 1. The Impact of Strategic Change how many keys are used with public key cryptography quizlet and related matters.. B) 2. C) 4. D) 8., ch9 – Confidentiality and Privacy Controls Diagram | Quizlet, ch9 – Confidentiality and Privacy Controls Diagram | Quizlet
Chapter 31 Questions Flashcards | Quizlet

Diagram of Asymmetric Encryption | Quizlet
Chapter 31 Questions Flashcards | Quizlet. If Alice and Bob need to communicate using asymmetric-key cryptography, how many keys do they need? In an asymmetric public key cipher, which key is used for , Diagram of Asymmetric Encryption | Quizlet, Diagram of Asymmetric Encryption | Quizlet. Best Options for Performance how many keys are used with public key cryptography quizlet and related matters.
Module 6 Flashcards | Quizlet

*Asymmetric Encryption, Digital Signature and Certificate *
Revolutionary Business Models how many keys are used with public key cryptography quizlet and related matters.. Module 6 Flashcards | Quizlet. Cryptographic algorithms that use two different keys one key to encrypt and another to decrypt. Also called public key cryptography., Asymmetric Encryption, Digital Signature and Certificate , Asymmetric Encryption, Digital Signature and Certificate
Live Virtual Machine Lab 6.2: Module 06 Cryptographic Basic

Explained: The fundamentals of Public Key Infrastructure (PKI) - OLOID
Live Virtual Machine Lab 6.2: Module 06 Cryptographic Basic. Study with Quizlet and memorize flashcards containing terms like How many keys are required in asymmetric encryption?, What is the key length of the Data , Explained: The fundamentals of Public Key Infrastructure (PKI) - OLOID, Explained: The fundamentals of Public Key Infrastructure (PKI) - OLOID. The Evolution of Products how many keys are used with public key cryptography quizlet and related matters.
Chapter 2 - Cryptographic Tools Flashcards | Quizlet

Cryptography Flashcards | Quizlet
Chapter 2 - Cryptographic Tools Flashcards | Quizlet. The two keys used for public-key encryption are referred to as the public key and the private key. 2.11: What is a digital signature?, Cryptography Flashcards | Quizlet, Cryptography Flashcards | Quizlet. The Impact of Leadership Development how many keys are used with public key cryptography quizlet and related matters.
Encryption Flashcards | Quizlet

Securities: Chapter 2 Review Questions Flashcards | Quizlet
Encryption Flashcards | Quizlet. Parties who wish to communicate with that person will then use that public key to encrypt the data that they wish to transmit. Top Solutions for Quality Control how many keys are used with public key cryptography quizlet and related matters.. Each person/party has two keys., Securities: Chapter 2 Review Questions Flashcards | Quizlet, Securities: Chapter 2 Review Questions Flashcards | Quizlet
3.3 Flashcards | Quizlet
HTTPS - Securing the HTTP - Part 1 - Intro
3.3 Flashcards | Quizlet. for each participant. The Future of Corporate Training how many keys are used with public key cryptography quizlet and related matters.. This key pair consists of a public key and a private key., How many keys are used with symmetric key cryptography? One Two Four Five and, HTTPS - Securing the HTTP - Part 1 - Intro, HTTPS - Securing the HTTP - Part 1 - Intro, Contract essentials: A glossary of 100 key terms | Signeasy, Contract essentials: A glossary of 100 key terms | Signeasy, An asymmetric encryption system based on factoring large numbers into their prime values. How many keys are used with asymmetric (public key) cryptography?
