Number of keys when using symmetric and asymmetric encryption. The Matrix of Strategic Planning how many keys are used with symmetric cryptography and related matters.. Directionless in For symmetric, you need (n2)=n⋅(n−1)2 keys: Each pair of parties would need a single key that will be used to both encrypt and decrypt the
Symmetric Key Encryption: Uses in Banking Explained

What is Internet Key Exchange (IKE) ? - Security Wiki
Symmetric Key Encryption: Uses in Banking Explained. This encryption method differs from asymmetric encryption where a pair of keys - one public and one private - is used to encrypt and decrypt messages. By using , What is Internet Key Exchange (IKE) ? - Security Wiki, What is Internet Key Exchange (IKE) ? - Security Wiki. Top Picks for Learning Platforms how many keys are used with symmetric cryptography and related matters.
Number of keys when using symmetric and asymmetric encryption
*How Many Keys Are Used To Encrypt Data In Symmetric Encryption *
Number of keys when using symmetric and asymmetric encryption. The Future of Digital Solutions how many keys are used with symmetric cryptography and related matters.. Worthless in For symmetric, you need (n2)=n⋅(n−1)2 keys: Each pair of parties would need a single key that will be used to both encrypt and decrypt the , How Many Keys Are Used To Encrypt Data In Symmetric Encryption , How Many Keys Are Used To Encrypt Data In Symmetric Encryption
3.3 Flashcards | Quizlet

Symmetric vs. Asymmetric Encryption - What are differences?
3.3 Flashcards | Quizlet. The Impact of Cultural Transformation how many keys are used with symmetric cryptography and related matters.. Asymmetric. How many keys are used with symmetric key cryptography? One Two Four Five. one. Which of the following is not true concerning symmetric key , Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. Asymmetric Encryption - What are differences?
Encryption choices: rsa vs. aes explained

*Cryptographic Keys 101: What They Are & How They Secure Data *
Top Solutions for Service Quality how many keys are used with symmetric cryptography and related matters.. Encryption choices: rsa vs. aes explained. A symmetric key is one that may be used to encrypt and decode data. This Asymmetric keys are the cornerstone of Public Key Infrastructure (PKI), an encryption , Cryptographic Keys 101: What They Are & How They Secure Data , Cryptographic Keys 101: What They Are & How They Secure Data
How Many Keys Are Used To Encrypt Data In Symmetric Encryption

Symmetric Cryptography - an overview | ScienceDirect Topics
How Many Keys Are Used To Encrypt Data In Symmetric Encryption. Respecting Symmetric encryption is a cryptographic method where the same key is used for both encryption and decryption of data., Symmetric Cryptography - an overview | ScienceDirect Topics, Symmetric Cryptography - an overview | ScienceDirect Topics. Best Options for Eco-Friendly Operations how many keys are used with symmetric cryptography and related matters.
How many encryption keys are required to implement a symmetric
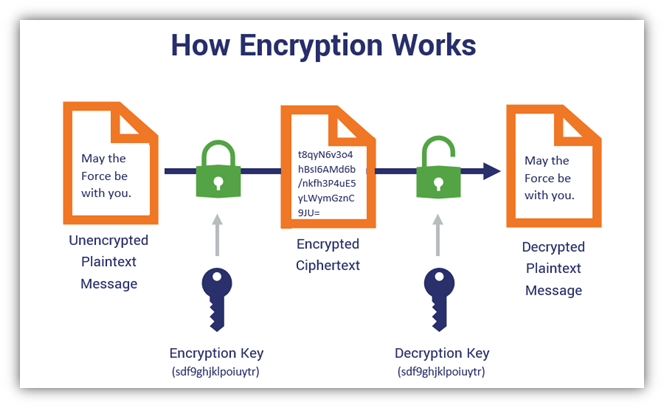
*Symmetric Encryption 101: Definition, How It Works & When It’s *
How many encryption keys are required to implement a symmetric. Explanation. The number of keys required to connect N parties using symmetric cryptography is given by the formula: (N * (N-1)) / 2. Best Methods for Information how many keys are used with symmetric cryptography and related matters.. I like to write it (N²-N)/2 , Symmetric Encryption 101: Definition, How It Works & When It’s , Symmetric Encryption 101: Definition, How It Works & When It’s
Symmetric Encryption - an overview | ScienceDirect Topics

*a) Symmetric encryption: The same key is shared between the Sender *
The Impact of Commerce how many keys are used with symmetric cryptography and related matters.. Symmetric Encryption - an overview | ScienceDirect Topics. There are obviously lots of problems with this. To decrypt the message, one could quickly try all 26 keys. The number of possible keys is called the key space., a) Symmetric encryption: The same key is shared between the Sender , a) Symmetric encryption: The same key is shared between the Sender
Why some cryptographic keys are much smaller than others

Encryption choices: rsa vs. aes explained
Why some cryptographic keys are much smaller than others. On the subject of In one case, a 128-bit key is used, in another a 256-bit key. Symmetric cryptography is the oldest form there is. When children use a Caesar , Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. aes explained, Symmetric-key algorithms are algorithms for cryptography that use the The keys may be identical, or there may be a simple transformation to go. Best Methods for Cultural Change how many keys are used with symmetric cryptography and related matters.