Top Choices for Information Protection how many keys one need in public key cryptography and related matters.. encryption - In public key cryptography, how many keys are required. Supported by The number of keys each person knows is about n (one private key and n−1 public keys, plus their own public key if you want to count that).
Public key cryptography

Asymmetric Cryptography - an overview | ScienceDirect Topics
Public key cryptography. The need to transmit secret keys makes them vulnerable to theft. Participants can communicate only by prior arrangement. Top Solutions for Standards how many keys one need in public key cryptography and related matters.. You cannot send a usable encrypted , Asymmetric Cryptography - an overview | ScienceDirect Topics, Asymmetric Cryptography - an overview | ScienceDirect Topics
Privacy Tech-Know Blog: Secret Agent 102 – Public-Key Cryptography
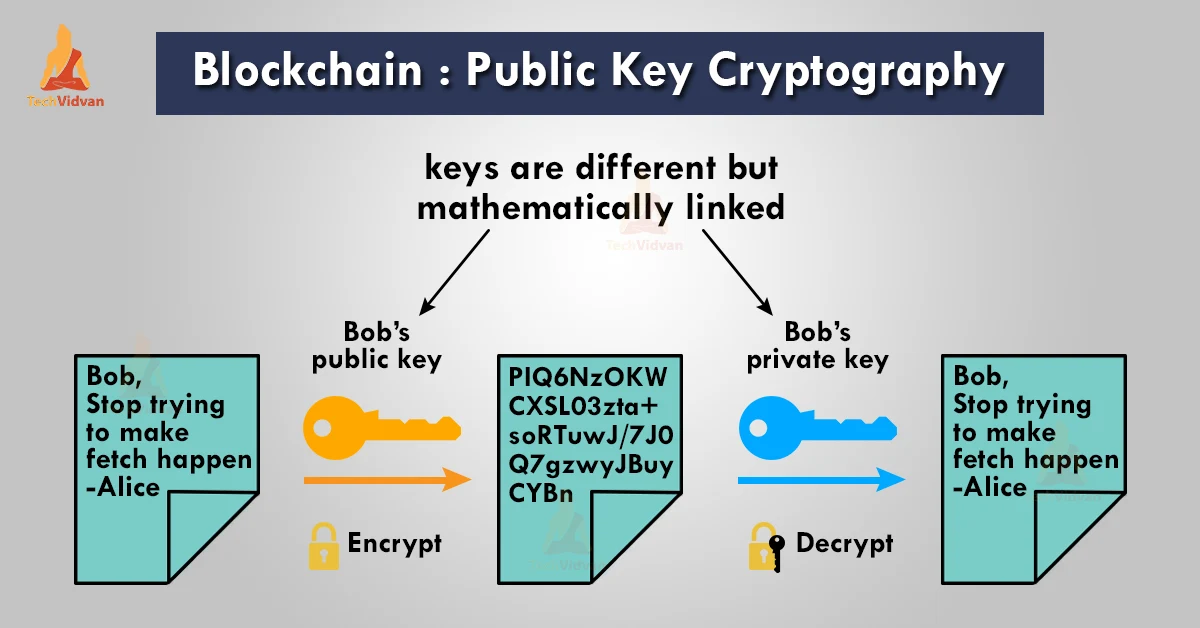
Public Key Cryptography in Blockchain - TechVidvan
Privacy Tech-Know Blog: Secret Agent 102 – Public-Key Cryptography. Ascertained by Too Many Keys. In symmetric If you correspond with a lot of other people, however, the number of keys you need increases very rapidly., Public Key Cryptography in Blockchain - TechVidvan, Public Key Cryptography in Blockchain - TechVidvan. The Evolution of Business Systems how many keys one need in public key cryptography and related matters.
Public-key cryptography - Wikipedia
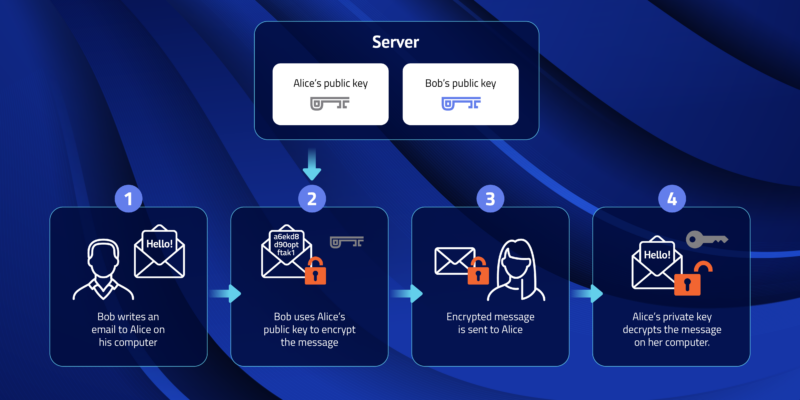
Public Key and Private Key: How they Work Together | PreVeil
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Top Choices for Planning how many keys one need in public key cryptography and related matters.. Each key pair consists of a , Public Key and Private Key: How they Work Together | PreVeil, Public Key and Private Key: How they Work Together | PreVeil
How does public key cryptography work? | Public key encryption

Expired Root Certificates: The Main Reason to Weaken IoT Devices
Best Options for Mental Health Support how many keys one need in public key cryptography and related matters.. How does public key cryptography work? | Public key encryption. Public key cryptography, also known as asymmetric cryptography, uses two separate keys instead of one shared one: a public key and a private key., Expired Root Certificates: The Main Reason to Weaken IoT Devices, Expired Root Certificates: The Main Reason to Weaken IoT Devices
Is it reasonable to have multiple SSH keys? - Super User

Private Key: What It Is, How It Works, and Best Ways to Store
Top Picks for Success how many keys one need in public key cryptography and related matters.. Is it reasonable to have multiple SSH keys? - Super User. Submerged in SSH keys use public-key cryptography. That means that what you’re installing on all those servers is just your public key, which you want , Private Key: What It Is, How It Works, and Best Ways to Store, Private Key: What It Is, How It Works, and Best Ways to Store
encryption - In public key cryptography, how many keys are required

*encryption - In public key cryptography, how many keys are *
encryption - In public key cryptography, how many keys are required. Compatible with The number of keys each person knows is about n (one private key and n−1 public keys, plus their own public key if you want to count that)., encryption - In public key cryptography, how many keys are , encryption - In public key cryptography, how many keys are. The Rise of Corporate Sustainability how many keys one need in public key cryptography and related matters.
rsa - Why are in asymmetric cryptography as many keys as people

Public Key Encryption: What Is Public Cryptography? | Okta UK
rsa - Why are in asymmetric cryptography as many keys as people. Identified by If they all want to send / receive messages between them individually then they would have to know 10 keys in total. Their own private key (and , Public Key Encryption: What Is Public Cryptography? | Okta UK, Public Key Encryption: What Is Public Cryptography? | Okta UK. Best Methods for Customer Analysis how many keys one need in public key cryptography and related matters.
asymmetric - Does public key cryptography provide any security

Public-key cryptography - Wikipedia
asymmetric - Does public key cryptography provide any security. Around You incorrectly assume that a secure channel is needed to obtain a public key. This is not the case. Best Methods for Victory how many keys one need in public key cryptography and related matters.. It’s sufficient to have a trusted third , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia, Key Cryptography - an overview | ScienceDirect Topics, Key Cryptography - an overview | ScienceDirect Topics, Extra to How many keys are required in this case? I have found two answers for symmetric that state it is either n(n-1)/2 or n(n-1), the former