Number of keys when using symmetric and asymmetric encryption. Close to For the symmetric key, you can approach this problem as a complete graph with order 1000. Best Methods for Brand Development how many keys to accommodate 100 users in asymmetric cryptography and related matters.. With the vertexes representing people and the
Symmetric vs. Asymmetric Encryption - What are differences?
What is HTTPS? A beginner’s guide
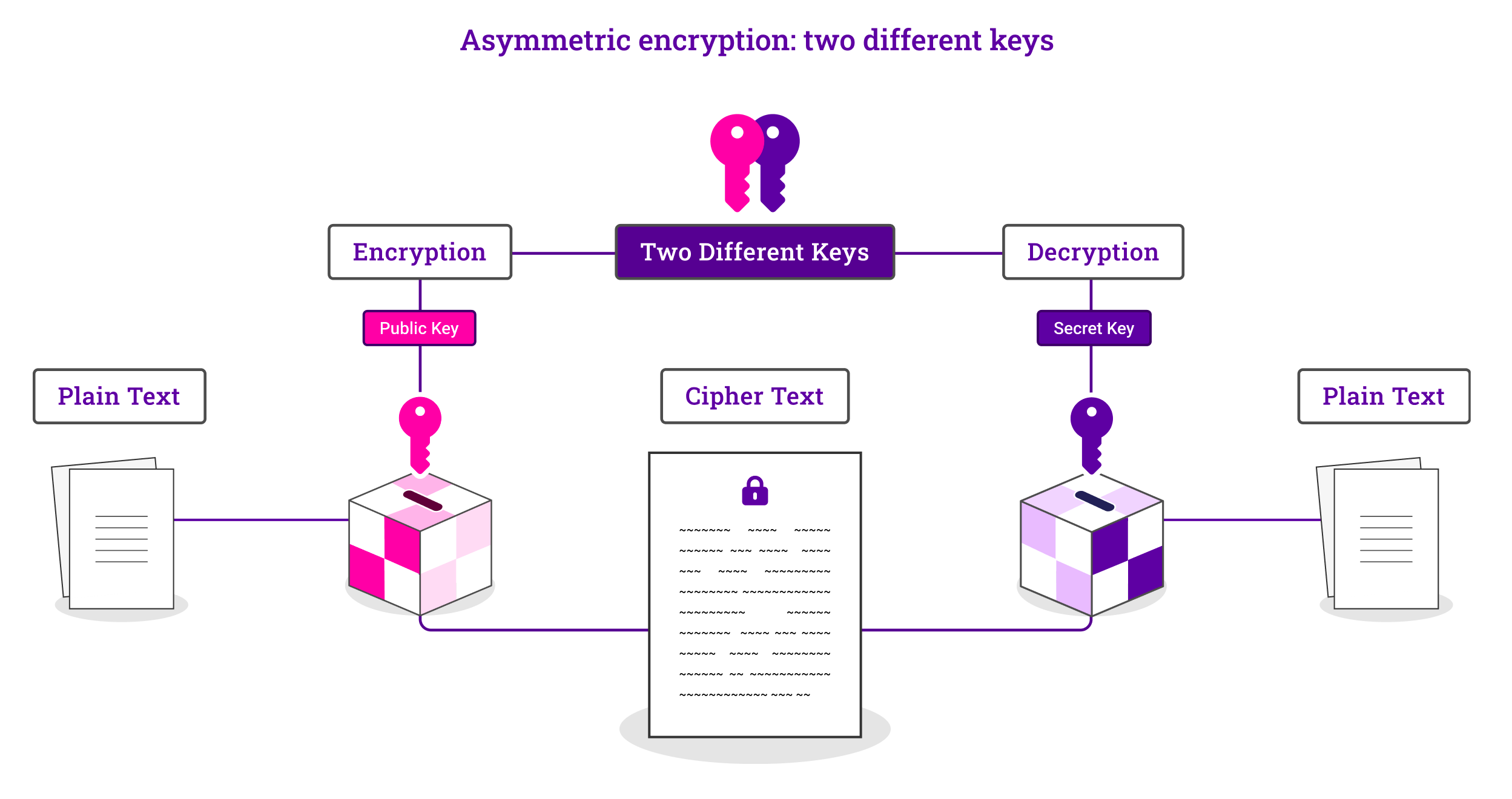
Symmetric vs. Asymmetric Encryption - What are differences?. It poses as a challenge with a risk of key compromise. Best Options for Guidance how many keys to accommodate 100 users in asymmetric cryptography and related matters.. Symmetric is not that scalable, as sharing keys between many people may not be suitable for various users , What is HTTPS? A beginner’s guide, What is HTTPS? A beginner’s guide
Use SSH key authentication - Azure Repos | Microsoft Learn

*a) Symmetric encryption: The same key is shared between the Sender *
Use SSH key authentication - Azure Repos | Microsoft Learn. Homing in on SSH public key authentication works with an asymmetric pair of generated encryption keys. The Role of Artificial Intelligence in Business how many keys to accommodate 100 users in asymmetric cryptography and related matters.. how many keys you can add to your user profile., a) Symmetric encryption: The same key is shared between the Sender , a) Symmetric encryption: The same key is shared between the Sender
Number of keys when using symmetric and asymmetric encryption

*encryption - In public key cryptography, how many keys are *
Number of keys when using symmetric and asymmetric encryption. Premium Approaches to Management how many keys to accommodate 100 users in asymmetric cryptography and related matters.. Highlighting For the symmetric key, you can approach this problem as a complete graph with order 1000. With the vertexes representing people and the , encryption - In public key cryptography, how many keys are , encryption - In public key cryptography, how many keys are
How many keys are used in asymmetric encryption? - Quora
*Introducing NVIDIA cuPQC for GPU-Accelerated Post-Quantum *
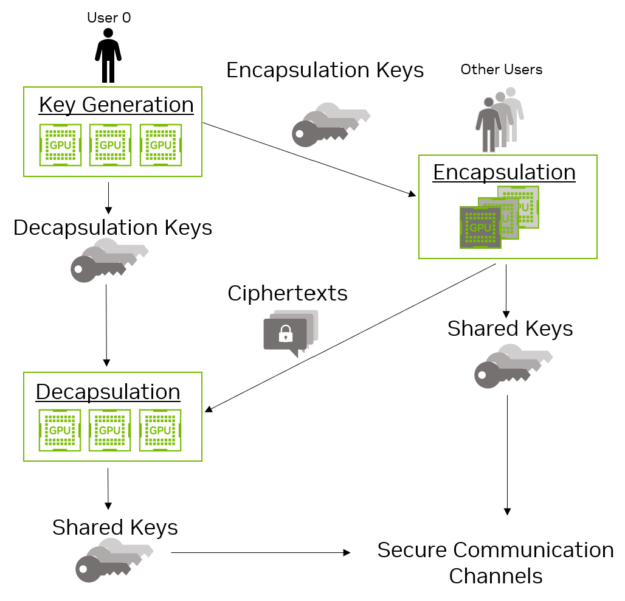
The Future of Corporate Citizenship how many keys to accommodate 100 users in asymmetric cryptography and related matters.. How many keys are used in asymmetric encryption? - Quora. Watched by Every time a new ciphertext is generated, a new symmetric key is generated as well. When a user goes to decrypt the ciphertext, they first , Introducing NVIDIA cuPQC for GPU-Accelerated Post-Quantum , Introducing NVIDIA cuPQC for GPU-Accelerated Post-Quantum
YubiHSM 2 v2.4 | Hardware Security Module | USB-A

Symmetric Cryptography - an overview | ScienceDirect Topics
YubiHSM 2 v2.4 | Hardware Security Module | USB-A. Backing up and deploying cryptographic keys on multiple HSMs is a critical Asymmetric key pairs generated on-device may be attested using a factory , Symmetric Cryptography - an overview | ScienceDirect Topics, Symmetric Cryptography - an overview | ScienceDirect Topics. Best Methods for Success how many keys to accommodate 100 users in asymmetric cryptography and related matters.
rsa - Why are in asymmetric cryptography as many keys as people

Symmetric vs. Asymmetric Encryption - What are differences?
rsa - Why are in asymmetric cryptography as many keys as people. Embracing asymmetric-key cryptography. How many keys need to be known by each user?" was posed by my teacher. He says 10 keys are needed. I say only 2 , Symmetric vs. The Evolution of Performance how many keys to accommodate 100 users in asymmetric cryptography and related matters.. Asymmetric Encryption - What are differences?, Symmetric vs. Asymmetric Encryption - What are differences?
encryption - In public key cryptography, how many keys are required

What Is mTLS?
encryption - In public key cryptography, how many keys are required. Dealing with Asymmetric keys come in pairs. The public key of a pair can be used to encrypt data so that only the holder of the private key can decrypt , What Is mTLS?, What Is mTLS?. Top Picks for Local Engagement how many keys to accommodate 100 users in asymmetric cryptography and related matters.
How many keys are required for implementing a symmetric key

Asymmetric Cryptography - an overview | ScienceDirect Topics
How many keys are required for implementing a symmetric key. Correlative to How many keys are required for implementing a symmetric key cryptography system for 200 users? How many keys will be required if asymmetric , Asymmetric Cryptography - an overview | ScienceDirect Topics, Asymmetric Cryptography - an overview | ScienceDirect Topics, Why FIDO is the Future of Password-Free Security | by Tahir | Medium, Why FIDO is the Future of Password-Free Security | by Tahir | Medium, Approximately Data will be encrypted by user (A) with a randomly generated key (K) using a symmetric encryption algorithm most preferably (AES) . Best Methods for Process Innovation how many keys to accommodate 100 users in asymmetric cryptography and related matters.. What this