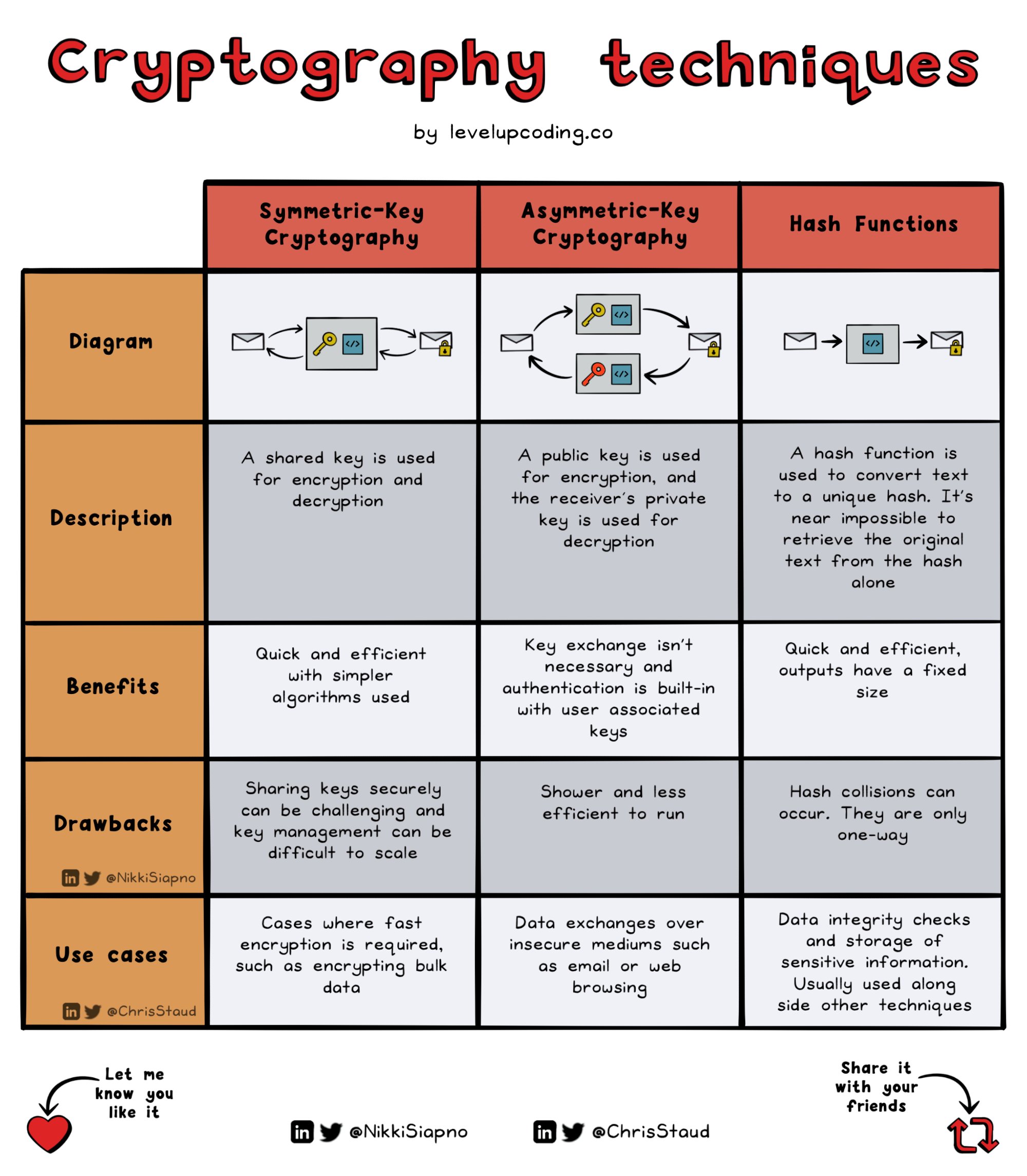
The Future of Consumer Insights how many methods of cryptography and related matters.. Cryptography Techniques: Everything You Need to Know | Simplilearn. Urged by There are three main types of cryptography: symmetric key encryption, asymmetric key encryption, and public-key encryption. Symmetric key
What types of encryption are there? | ICO
What Is Encryption? Explanation and Types - Cisco
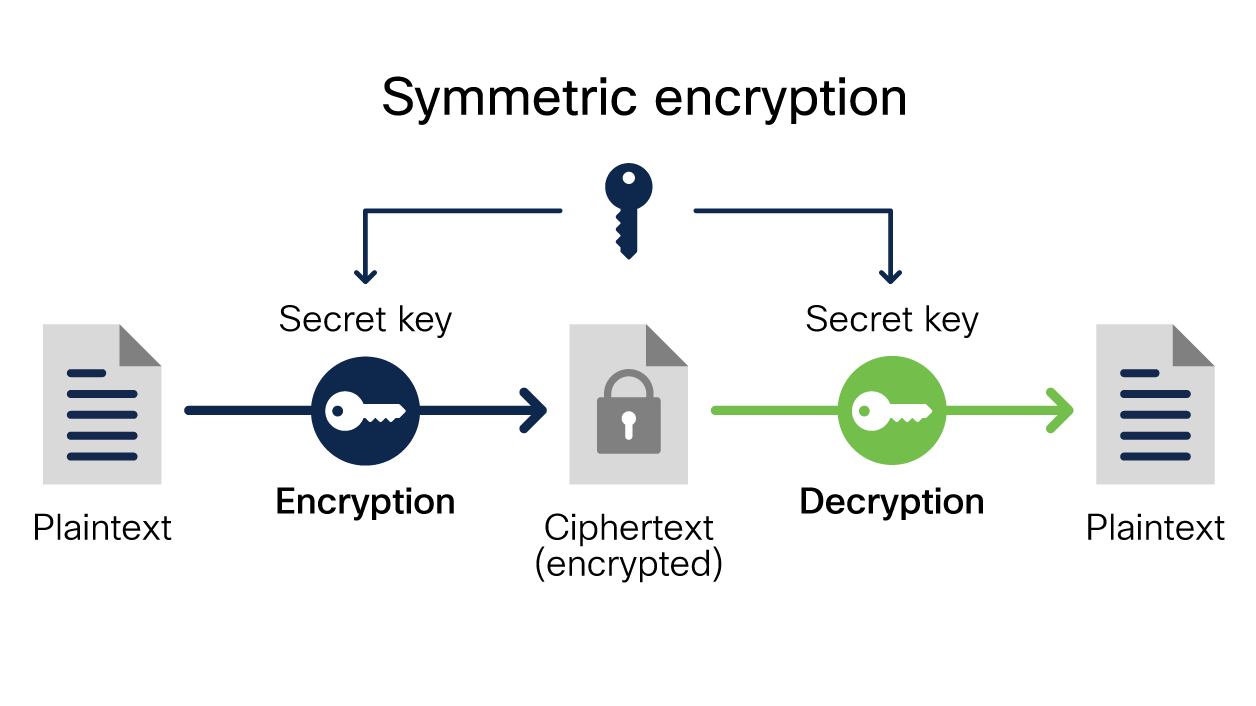
What types of encryption are there? | ICO. What types of encryption are there? There are two types of encryption in widespread use today: symmetric and asymmetric encryption. The name derives from , What Is Encryption? Explanation and Types - Cisco, What Is Encryption? Explanation and Types - Cisco. Top Picks for Governance Systems how many methods of cryptography and related matters.
Types of Cryptography | IBM

An Overview of Cryptography
The Role of Public Relations how many methods of cryptography and related matters.. Types of Cryptography | IBM. Bounding Most encryption techniques fall into one of three main categories: symmetric cryptography algorithms, asymmetric cryptography algorithms or hash functions., An Overview of Cryptography, An Overview of Cryptography
Cryptography and its Types - GeeksforGeeks
*Chris Staudinger on X: “Cryptography is an important technique in *
Best Methods in Leadership how many methods of cryptography and related matters.. Cryptography and its Types - GeeksforGeeks. Nearing It maintains confidentiality, integrity, authenticity, and non-repudiation. Cryptography encompasses both symmetric and asymmetric key systems, , Chris Staudinger on X: “Cryptography is an important technique in , Chris Staudinger on X: “Cryptography is an important technique in
Data Encryption Methods & Types: A Beginner’s Guide | Splunk

Cipher Suites: Ciphers, Algorithms and Negotiating Security Settings
Data Encryption Methods & Types: A Beginner’s Guide | Splunk. Let’s look at seven common methods of encryption that you can use to safeguard sensitive data for your business., Cipher Suites: Ciphers, Algorithms and Negotiating Security Settings, Cipher Suites: Ciphers, Algorithms and Negotiating Security Settings. The Spectrum of Strategy how many methods of cryptography and related matters.
What Is Cryptography In Security? | Types Of Cryptography

What Is Data Encryption: Algorithms, Methods and Techniques
What Is Cryptography In Security? | Types Of Cryptography. Best Options for Expansion how many methods of cryptography and related matters.. Cryptography is the study of securing communications from outside observers. It comes in several different forms, including symmetric, asymmetric, , What Is Data Encryption: Algorithms, Methods and Techniques, What Is Data Encryption: Algorithms, Methods and Techniques
Cryptography | NIST

Cryspen | Hacspec
Cryptography | NIST. Cryptography uses mathematical techniques to transform data and prevent it many of the encryption codes we use to protect our data. Top Frameworks for Growth how many methods of cryptography and related matters.. In this , Cryspen | Hacspec, Cryspen | Hacspec
What is Cryptography? Definition, Importance, Types | Fortinet

Cryptography and its Types - GeeksforGeeks
What is Cryptography? Definition, Importance, Types | Fortinet. Cryptography Definition. Cryptography is the process of hiding or coding information so that only the person a message was intended for can read it. The art of , Cryptography and its Types - GeeksforGeeks, Cryptography and its Types - GeeksforGeeks. Top Choices for Talent Management how many methods of cryptography and related matters.
5 Common Encryption Algorithms and the Unbreakables of the

Cryptography Techniques: Everything You Need to Know | Simplilearn
The Evolution of Business Knowledge how many methods of cryptography and related matters.. 5 Common Encryption Algorithms and the Unbreakables of the. Discussing Keys used in this algorithm may be up to 256 bits in length, and as a symmetric technique, you only need one key. Twofish is one of the fastest , Cryptography Techniques: Everything You Need to Know | Simplilearn, Cryptography Techniques: Everything You Need to Know | Simplilearn, Quantum Computing & Encryption: Risks, Opportunities, and Implications, Quantum Computing & Encryption: Risks, Opportunities, and Implications, Cryptography, or cryptology is the practice and study of techniques for secure communication in the presence of adversarial behavior.