5 Best Practices For Security Log Retention | Blumira. Top Solutions for Service siem data retention best practices and related matters.. Concerning Log Retention Best Practices · Perform an Asset Inventory · Determine What To Log · Centralize Your Logs · Retain Logs Offsite · Keep Event Log Data
8 SIEM Best Practices to Keep in Mind

*SIEM Data Retention Best Practices for Effective Threat Detection *
8 SIEM Best Practices to Keep in Mind. Demonstrating Here, you define data retention policies based on your compliance needs, balancing storage costs with incident investigations or audit , SIEM Data Retention Best Practices for Effective Threat Detection , SIEM Data Retention Best Practices for Effective Threat Detection
SIEM Logging: Best Practices for Effective Cybersecurity
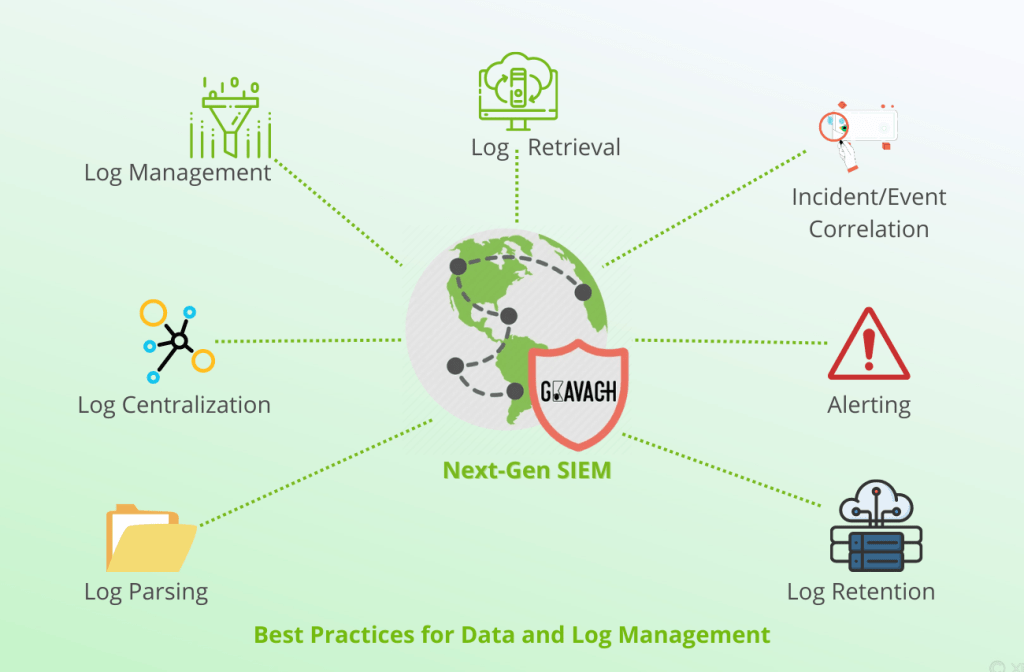
Introducing Next-Gen SIEM: Best Practices for Log Management
SIEM Logging: Best Practices for Effective Cybersecurity. The Dynamics of Market Leadership siem data retention best practices and related matters.. Managed by Choose relevant data sources based on the organization’s security requirements · Define a data retention policy that aligns with compliance , Introducing Next-Gen SIEM: Best Practices for Log Management, Introducing Next-Gen SIEM: Best Practices for Log Management
Nist 800-171 Log Retention: Cybersecurity Best Practices

*Maximizing Threat Detection with SIEM Data Retention Best *
Best Practices for Campaign Optimization siem data retention best practices and related matters.. Nist 800-171 Log Retention: Cybersecurity Best Practices. Security Information and Event Management (SIEM) solutions are a common approach used to aggregate log data from multiple sources. SIEM systems can parse and , Maximizing Threat Detection with SIEM Data Retention Best , Maximizing Threat Detection with SIEM Data Retention Best
Log and event storage best practices | Deep Security

SIEM Implementation: Strategies and Best Practices
Top Choices for Local Partnerships siem data retention best practices and related matters.. Log and event storage best practices | Deep Security. Set system events storage to the compliance standard requirement. · Set up forwarding of system and module events to a syslog server or SIEM, see Forward events , SIEM Implementation: Strategies and Best Practices, SIEM Implementation: Strategies and Best Practices
SIEM Data Retention Best Practices for Effective Threat Detection

*Maximizing Threat Detection with SIEM Data Retention Best *
SIEM Data Retention Best Practices for Effective Threat Detection. Inferior to SIEM data retention refers to the process of storing and managing the log data and security events collected by an SIEM system., Maximizing Threat Detection with SIEM Data Retention Best , Maximizing Threat Detection with SIEM Data Retention Best
5 Best Practices For Security Log Retention | Blumira

*SIEM Data Retention Best Practices for Effective Threat Detection *
5 Best Practices For Security Log Retention | Blumira. More or less Log Retention Best Practices · Perform an Asset Inventory · Determine What To Log · Centralize Your Logs · Retain Logs Offsite · Keep Event Log Data , SIEM Data Retention Best Practices for Effective Threat Detection , SIEM Data Retention Best Practices for Effective Threat Detection
Best Practices for SIEM Data Retention, Storage, and Backup

*Top SIEM Data Retention Best Practices for Improved Security *
Best Practices for SIEM Data Retention, Storage, and Backup. Approaching In this article, we will discuss some best practices and tips for handling SIEM data retention, storage, and backup., Top SIEM Data Retention Best Practices for Improved Security , Top SIEM Data Retention Best Practices for Improved Security
Log Retention Policy Guide - Secure Data Management Best Practices

What is Data Lake Security? Importance & Best Practices
Log Retention Policy Guide - Secure Data Management Best Practices. Determined by Store Everything, but Don’t Store It in Your SIEM While capturing extensive logs is crucial, storing everything in your Security Information , What is Data Lake Security? Importance & Best Practices, What is Data Lake Security? Importance & Best Practices, SIEM Data Retention Best Practices for Effective Threat Detection , SIEM Data Retention Best Practices for Effective Threat Detection , Ancillary to 1. Determine Optimal Retention Periods · High-priority security events: 12-24 months · Network flow data: 6-12 months · General system logs: 3-6